A public key is generated in public key encryption cryptography

A public key is generated in public key encryption cryptography which utilizes asymmetric-key encryption algorithm. The primary focus of public keys is to convert a message into an unreadable format. That unreadable format is decrypted using a different, but matching, private key. Both public keys and private keys are paired to enable secure communication between two people.
Public Key Explained
A Public Key can be placed in an open access directory to decrypt the digital signature of the sender. The public of the recipient is used to encrypt the sender’s message. Public Key Infrastructure produces and private keys.
The open access public key can even be emailed to the reliable users and contacts. PGP (Pretty Good Privacy) is the most popular form of public key cryptography. The PGP keys are accumulated in a public-server directory to allow public key sharing. PGP server directory keys can be updated, but can’t be removed.
You May Also Read: Private Key
What Does Public Key Cryptography Mean?
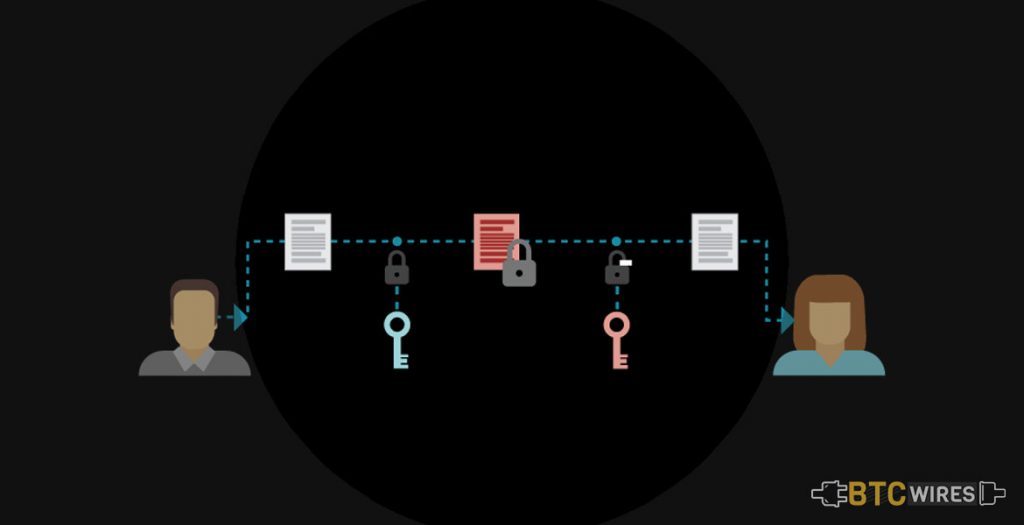
Public Key Cryptography is an encryption technique utilizing a paired public as well as a private key algorithm for secure data communication. A message sender uses a public of the message recipient to encrypt a message. Only the recipient’s private key can be used to decrypt the sender’s message.
RSA are the two types of PKC algorithms. RSA is the acronym form that is named after this algorithm’s investors: Rivest, Shamir and Adelman, and DSA (Digital Signature Algorithm). Public Key Cryptography encryption evolved to meet the increasing secure communication demands of the multiple industries, including the military.
PKC is often referred to as asymmetric encryption, public key encryption, asymmetric cipher, asymmetric cryptography, Diffie-Hellman encryption, and asymmetric key encryption.
You May Also Read: Irreversible Transactions
How Does The Encryption Work?
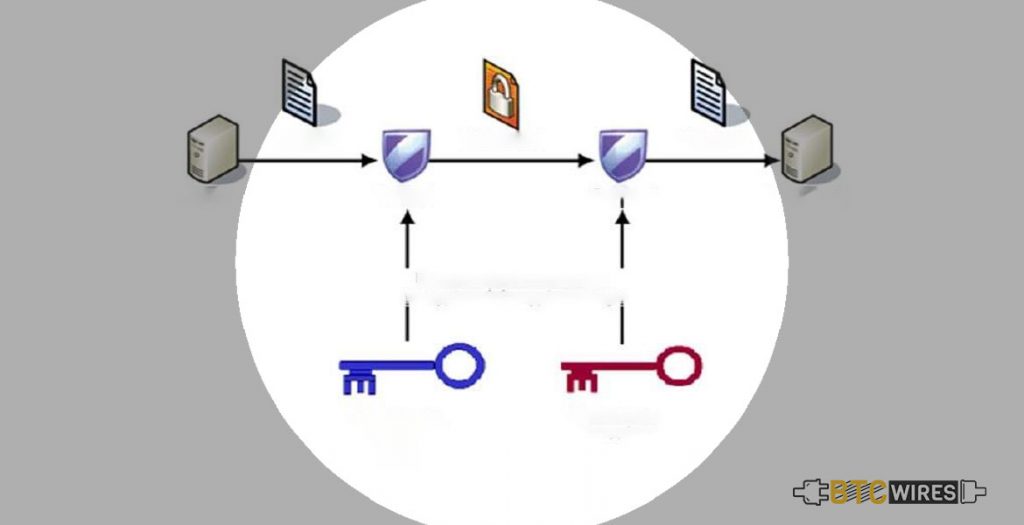
One of the weaknesses of symmetric key encryption is that two users who are trying to communicate with each other need a secure approach to do so. Else, the bad doers can easily pluck the information from the stream.
Public key encryption, also known as asymmetric key encryption, uses two different keys at one time – a combination of a public key as well as a private key. The private key is recognized only to your computer, whereas the public is given by your computer to any computer what wishes to communicate securely with it. A computer must have the public key to decode an encrypted message. The public key is provided by the originating computer and its own private key.
Though a message sent from one computer to the other will not be considered secure as the public key used for encryption is available to anyone, yet anyone who picks it up cannot read it without the private key. The key pair is based on the prime numbers of long length. This is what makes the system extremely secure since there is essentially an infinite number of prime numbers available. This means that there are nearly infinite possibilities for the keys. PGP allows you to encrypt almost anything.
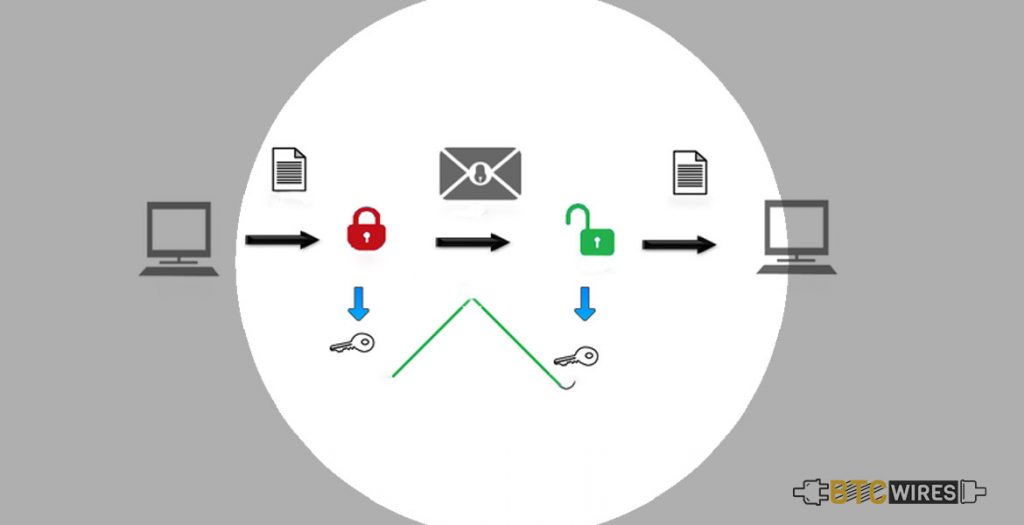
The sending computer encrypts the document using a symmetric key, then encrypts this key with the public key of the receiving computer. The receiving computer utilizes its private key for decoding the symmetric key. Then, it uses the symmetric key for decoding the document.
You May Also Read: How To Secure Crypto Wallets?
The Commencement of Public Key Encryption
For implementing public key encryption on a large scale requires a unique approach. This is where digital signatures come in. A digital signature or digital certificate is mainly a unique piece of code or a large number saying that the web service is reliable with an independent source recognized as a certificate authority. This authority acts as a middleman which both computers trust. This then confirms that each computer is the fact and then offers the public keys of each computer to the other. That’s really a unique nature of Blockchain Technology.
Here are a Few Articles for you to Read Next:

