Cryptography was once exclusive to the realms of government, academia

Cryptography was once exclusive to the realms of government, academia and the military.
However, with recent technological advancements, cryptography has started permeating all facets of everyday life.
Everything from your smartphone to your banking depends on cryptography to keep your data safe and your livelihood secure.
With the vast amounts of personal data circulating the internet, it is more important now than ever to learn how to protect yourself successfully from the individuals with ill intentions.
You May Also Read: The Cryptography That Blockchain Runs On
Why Does Cryptography Matter?

Let’s start with discussing the only real alternative to cryptography – Obfuscation. Obfuscation is defined as “the act of making something unclear, obscure, or unintelligible.”
In order to transmit a secure message, you should better hold back some of the data required to understand the message, which means that it would only take one person with knowledge of the original message to divulge the missing pieces to the general population.
With cryptography, a specific key and numerous calculations are needed. Even if someone knew the encryption method used, they would not be able to decrypt the message without the corresponding key, making your information much more secure.
You May Also Read: Are Cryptocurrencies Threat to Banking?
Types of Cryptography
There are four types of cryptography in use today, each with its own unique advantages as well as disadvantages.
1. Hashing

Hashing is a type of cryptography which changes a message into an unreadable string of text for verifying the message’s contents, not hiding the message itself.
This type of cryptography is most commonly used for protecting the transmission of software and large files where the publisher of the files or software provides them for download.
The reason for this is that, while it’s easy to calculate the hash, it’s highly difficult to find an initial input that will offer an exact match for the desired value.
Currently, the most used cryptographic hash functions are MD5 and SHA-1. However, because of these algorithm’s multiple weaknesses, most new applications are transitioning to the SHA-256 algorithm rather than its weaker predecessors.
2. Symmetric Cryptography
Symmetric Cryptography is the system with which you are perhaps most familiar.
This is the type of cryptography that uses a single key to encrypt a message and then decrypt that message upon delivery.
Since symmetric cryptography needs that you have a secure channel to deliver the crypto key to the recipient. It’s all but useless for transmitting the data.
As such, its primary application is the protection of resting data.
Most modern symmetric cryptography depends on a system called AES or Advanced encryption Standards.
While the traditional DES models were the industry norm for so long, DES was publicly attacked and broken in 1999 causing the National Institute of Standards and Technology to host a selection process for a stronger and more updated model.
After an arduous 5 year competition between 15 different ciphers, including RC6 from RSA Security, MARS from IBM, Twofish, Serpent, and Rijndael, the NIST selected Rijndael as the winning cipher.
Then, it was standardized across the country, earning the name AES. this cipher is still widely used today and even implemented by the NSA for guarding top secret information.
3. Asymmetric Cryptography
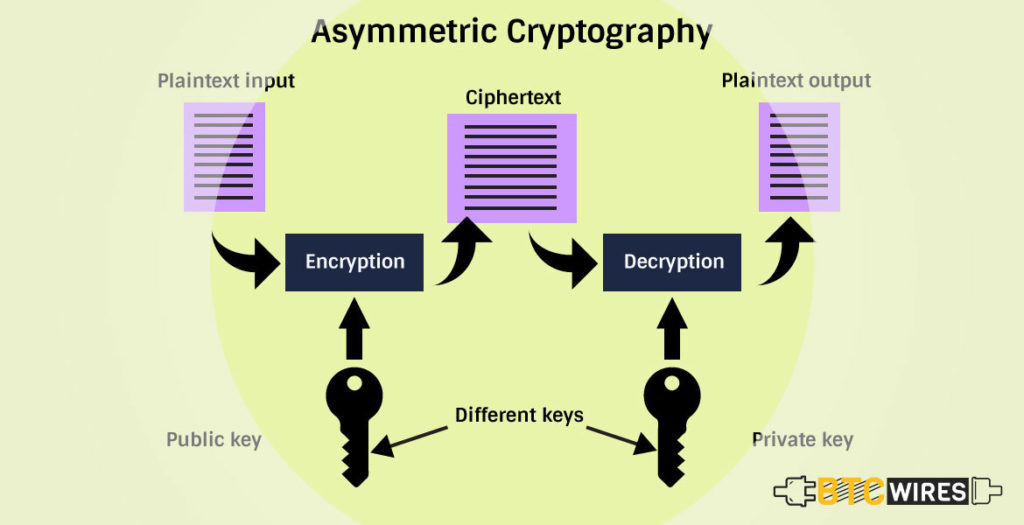
As the name implies, Asymmetric Cryptography uses two different keys for both encryption and decryption, as opposed to the single key used in symmetric cryptography.
The first key is a public key that is used to encrypt the message, and another is a private key used to decrypt them.
The excellent part about this system is that only the private key is used to decrypt the encrypted messages sent from a public key.
While this sort of cryptography is a little more complicated, you are likely familiar with a number of its practical applications.
4. Key Exchange Algorithms
A key exchange algorithm is used to safely exchange the encryption keys with an unknown party.
Different from the other forms of encryption, you aren’t sharing data amid the key exchange. The end goal is to create an encryption key with another party which can later be used with the aforementioned forms of cryptography.
4 Types of Cryptographic Functions
Now, that you comprehend a little bit more about the different types of cryptography, many of you are probably wondering how it is applied in the world today.
There are 4 primary ways that cryptography is used in information security. These 4 applications are known as “cryptographic functions.”
1. Authentication

When you use the right cryptographic system, you can establish the identity of a system effortlessly.
The go-to instance of this is the SSL certificate of a web server that offers proof to the user that they are associated with the right server.
The identity in the question is not the user, but rather the cryptographic key of that user. This means that the more secure the key, the surer the identity of the user and vice-versa.
2. Nonrepudiation
This notion is very important for anyone using or developing financial or e-commerce applications.
One of the big issues that e-commerce pioneers faced was the ubiquitous nature of users would refute transaction once they had dependably occurred.
Cryptographic tools were developed to make sure that each unique user had surely made a transaction request that would be irrefutable at a later time.
3. Confidentiality

With information leaks and a seemingly endless number of privacy scandals making the headlines, keeping your data private is probably one of your biggest concerns.
This is the exact function whereby cryptographic systems were originally developed.
With the right encryption tools, users can guard sensitive company data, personal medical records or simply lock their computer with a simple password.
4. Integrity
Another important use of cryptography is to make sure that the data is not viewed or altered amid the transmission or storage.
The most common way to accomplish data integrity through cryptography is by using cryptographic hashes for safeguarding information with a secure checksum.
You May Also Read: Bitcoin History
Conclusion
By developing a greater comprehension of the common encryption methods and cryptography algorithms in circulation, you will be better equipped for protecting yourself from potential cyber attacks as well as breaches in data security.
Though cryptography isn’t perfect, it’s crucial to make sure that the continued security of your personal information. And with the rapidly evolving landscape of modern data, this topic is even more important now than ever before.
Here are a Few Articles for you to Read Next:
