RSA is one of the most well-known cryptographic algorithms and

RSA is one of the most well-known cryptographic algorithms and is used quite commonly to transmit data in a securely encrypted way. Here is a brief beginner’s guide to RSA to get a general understanding of this algorithm.
What is RSA?
RSA is named after the ones who came up with it: Rivest, Shamir and Adleman. It is one of the pioneering public-key crypto algorithms. In this kind of an algorithm, the key for encryption is open to all but the decryption key is what is kept under wraps and is thus called the private key. This is why the algorithm is also known as an asymmetric one. The asymmetry is based upon the principle that finding the factors of two large prime numbers is immensely hard to achieve. The users of RSA algorithm can create and make public one half of the key pair, that is, the public key, which is based on the calculation of two substantially large prime numbers, in addition to an auxiliary value. These numbers must be kept secure and private. Given that the public key is readily available to anybody for encryption, anyone might be able to crack the system if they manage to discover the prime numbers. With that knowledge, they can easily decrypt all messages.
RSA, as an algorithm, is not an excessively speedy one. Therefore, direct encryption of data using this algorithm is not all that common. However, what is common is using RSA to pass on encrypted forms of shared keys to cryptographic algorithms that are symmetric in nature, to speed up the process of encrypting and decrypting a large volume of data and messages. Thus, this basically implies that despite not being supremely swift itself, this algorithm can aid those that are, and enable secure data transmissions easily and effectively.
How does the RSA Algorithm work?
There are four steps to this process that are discussed as follows:
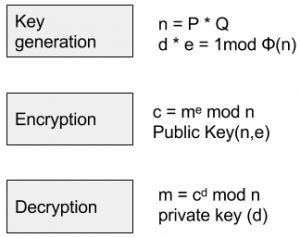
Key Generation
In generating the public and private keys, the principle that is used is that a secure system can be built by identifying three large positive integers, referred to as e,d and n so that their modular exponentiation for message m, when 0 ≤ m < n, will mean that even know e, n or m will make it nearly impossible to find d. For some operations, what is done is the order of the two exponentiations found in this equation, is changed. The letter d represents the private key and is the gateway to breaching this system.
Key Distribution
For messages to be exchanged among people, concerned parties must be aware of the public key so they can encrypt messages they are sending. However, each user will have a specific private key d that is never to be disclosed.
Encryption
For the process of encryption, the sender converts the message from plaintext M into a ciphertext m based on the system of modular exponentiation mentioned in the key generation step. The padding scheme or the decided-upon and reversible scheme for encrypting messages is followed and c, the ciphertext is generated, which equals to m to the power of e.
Decryption
From c, m can be discovered by the recipient using private key d. The padding scheme is simply revered by computing c to the power of d is equal to m to the power of e, whole to the power of d, further equal to m. Thus, in this way, ciphertext is turned back to plaintext.
To all these messages, signature can be added by generating a hash value of the same and raising that value to the power of the private key d.
Thus, though this processes, it becomes a secure algorithm so that it becomes rather hard to attack RSA.
